Some time ago I was presented with a very interesting question, how do I harden a Linux system without having to make wild guesses?
The answer was lynis, a program that scans your Linux system, highlights potentially dangerous configurations, and even suggests improvements.
Why Use Lynis to Secure Linux?
lynis helps you identify system vulnerabilities with concrete suggestions for remedial actions. It prevents guesswork and ensures you can systematically secure your Linux server.
How Do I Install lynis Using Git?
1. First, we need to download lynis using git to ensure we have the latest version. For our example, we’re using Ubuntu 24.04. Before proceeding, install git by running:
apt update; apt install git -yNote: The semicolon (;) separates one command from another so they will run in succession.
2. Once git is installed, clone the lynis repository by typing inline code:
git clone https://github.com/CISOfy/lynis.gitNote: Wherever you run this command, the repository will be cloned in that directory, so be mindful of your location.
How Do I Run lynis on Ubuntu 24.04?
1. Change into the lynis directory and run lynis by typing:
sudo ./lynis audit system2. The process can take a variable amount of time depending on your system and resources. You will see progress as it goes through all the default options.
3. After it finishes, a report is saved in the /var/log folder. To view the most important items (warnings or suggestions), run:
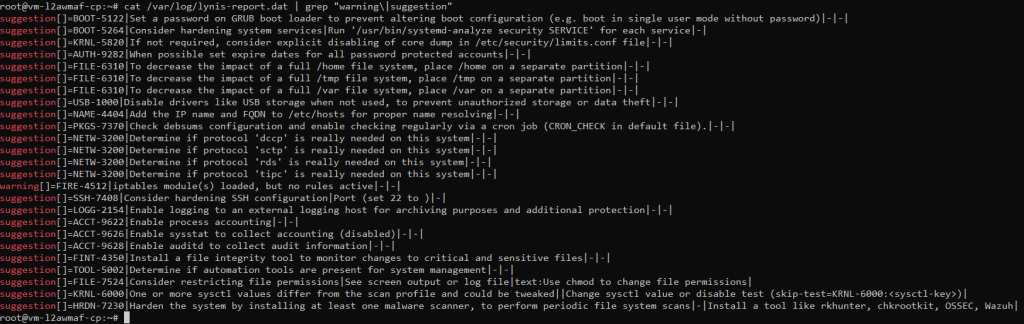
grep "warning\|suggestion" /var/log/lynis-report.dat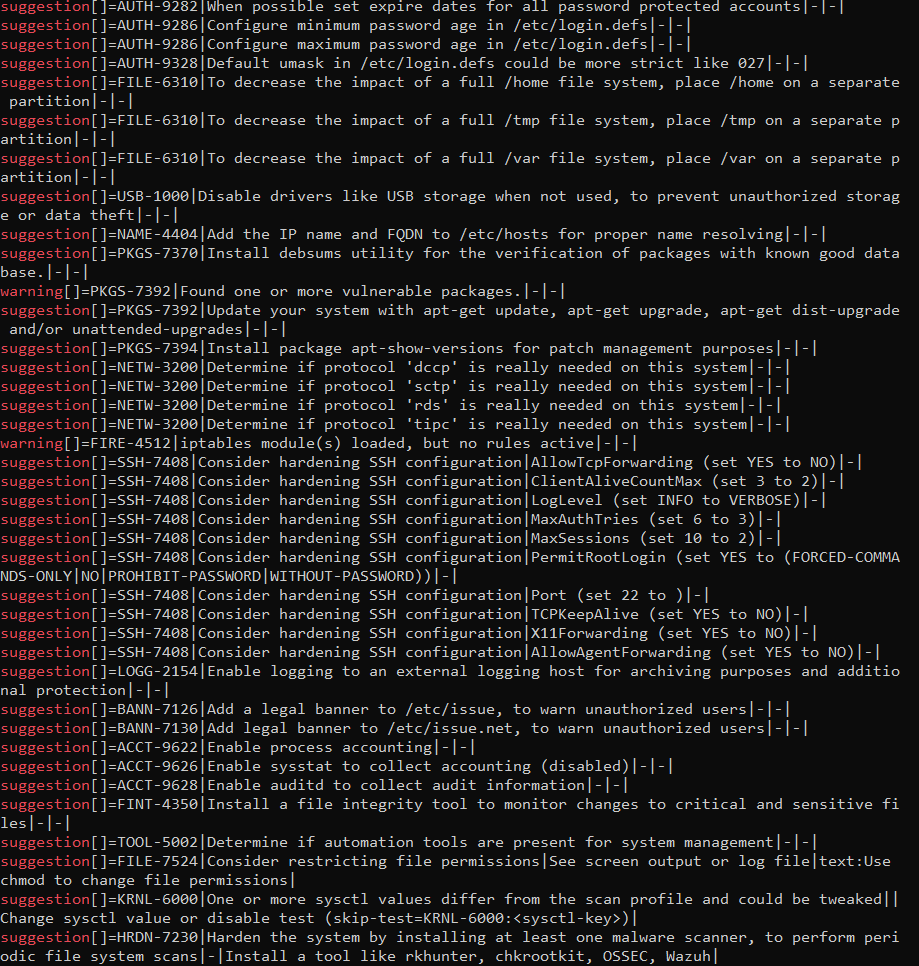
The screenshot above is an example of the information returned by lynis in its report. After running a script that automatically fixes some of these items, the list becomes much shorter. (Keep in mind that the list shown is longer than what is captured in the screenshot.)
Can I Automate Fixes With a Script?
Yes, there’s a script that addresses some of lynis’s findings automatically. It can be downloaded via git:
git clone https://github.com/vicosurge/Lynis-autofix.gitWe did not fix all the findings from lynis. It’s important to exercise caution when running any script that makes automatic changes – especially on production systems that have been running for a while.
What About Other Security Measures Like Log Collection?
lynis also mentions critical points about log collection, file integrity monitoring, and malware scanning, suggesting tools like OSSEC or Wazuh. In another instance, we will install Wazuh and configure it to properly monitor our hosts.
By following these steps and using lynis along with its automated scripts, you can significantly harden a Linux system without guesswork while maintaining a clear view of your server’s security posture.

